Indo-Pak & Israel-Iran: Cyber Wars Follow the Same Script?
-
 Shankar Jayaraman
Shankar Jayaraman - 28 Jun, 2025

Cyber attacks on critical infrastructure are no longer secondary acts of disruption, they are now front-line tactics in modern warfare. The cyber war between Iran and Israel seems to mark a shift in modern warfare, where digital attacks are becoming just as important as those on the ground.
This cyber battle does not differ much from the India-Pakistan cyber war in relation to the Operation Sindhoor in 2025, in which digital attacks have accompanied missile strikes after the Pahalgam terror attack incident. Both face state-backed APT groups alongside hacktivists in an espionage, sabotage, and information warfare exercise.
The research shows India’s national cyberspace attacks are characterized mainly by attack which consists of localized but intense cyber offenses towards crucial areas such as defense, government, telecom, notably visible website defacements as well as DDoS attacks that are not global. However, the India-Pakistan cyber war involves attacks on massive-scale financial institutions and critical civilian infrastructure which result in global spillover of risks.
These two conflicts also indicate that modern cyber warfare binds itself more to traditional military confrontations, taking digital means to disrupt, intimidate, and influence not only adversaries but global audiences. Such scenarios highlight the increasing significance of cyber resilience, intelligence sharing, and compliance with cyber security frameworks against a rising tide of hybrid threats in a globalizing world. As cyber attacks on critical infrastructure increase in scale and precision, safeguarding civilian systems becomes an international priority.
These campaigns reveal how hybrid warfare now includes a digital front. Before we compare specific tactics, it’s important to understand how these attacks unfold in real-world operations.
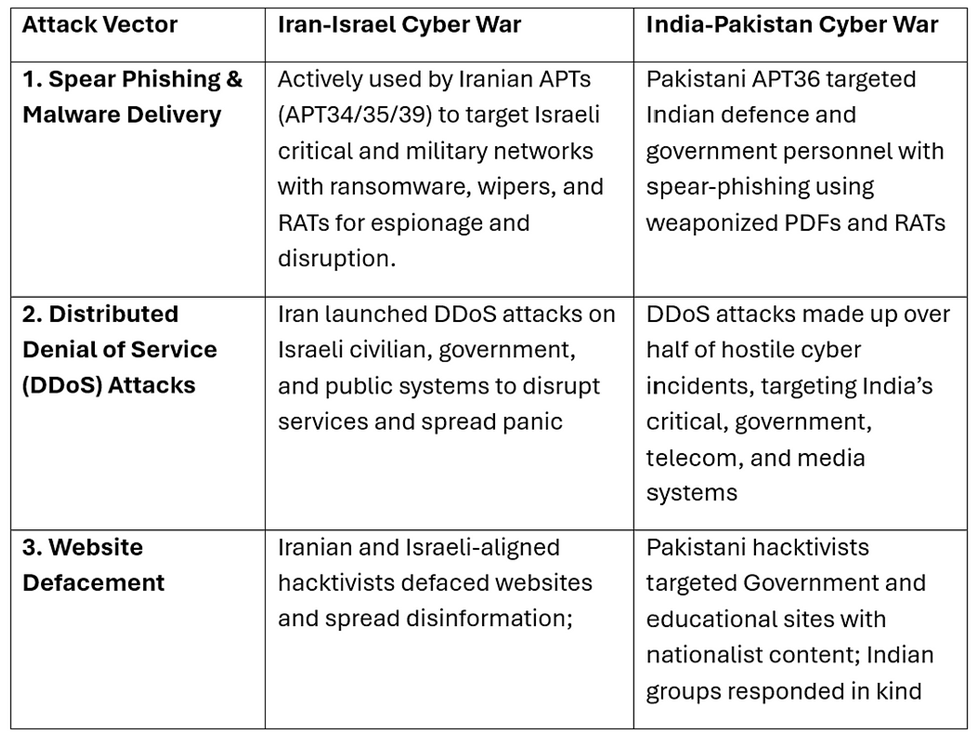
The following is a comparison of the three main attack vectors used during the Iran–Israel cyber war and India’s Operation Sindhoor on Pakistan:
Conclusion
The core attack vectors are similar: phishing/malware, DDoS, and defacements; however, the scale, sophistication, and integration with kinetic operations differ with each geopolitical context and cyber capabilities of actors. What remains consistent is the strategic focus on cyber attacks on critical infrastructure as a means of exerting pressure and destabilization.
When it comes to state-level cyber warfare, embracing thorough GRC practices is essential for protecting critical infrastructure, safeguarding sensitive data, and minimizing the ripple effects of cyberattacks on both civilian populations and allied nations. In essence, GRC acts as a strategically that not only lowers cyber risk exposure but also fosters the operational resilience needed to endure and bounce back from complex cyber conflicts.
CISOGenie: Your GRC Ally in AI-powered Risk Management
CISOGenie stands as your trusted partner in navigating the intricate GRC landscape of today. By bringing together IT and OT compliance, utilizing genuine AI for automated evidence gathering, and offering ongoing risk insights, our platform significantly cuts down your organization’s security risks. This shift not only enhances your security stance but also ensures smooth operations and strengthens your brand’s reputation in a constantly changing threat landscape.