All Blogs
-
 Balachandran Sivakumar
Balachandran Sivakumar - 31 Dec, 2025
CCM — The Definitive Path to Control testing and Operational Effectiveness
For decades, compliance has been treated as a periodic event. An audit approaches, spreadsheets mult ...

-
 Balachandran Sivakumar
Balachandran Sivakumar - 19 Dec, 2025
AI didn’t invent code generation. It just raised the abstraction
The past 8 to 10 months, we have seen AI agents become “software engineers” — They are being increas ...
-
 Balachandran Sivakumar
Balachandran Sivakumar - 19 Dec, 2025
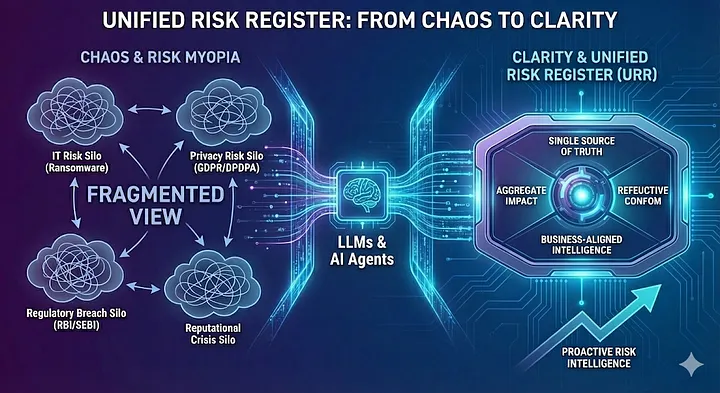
Unified Risk Register (URR): From Siloed Risk Management to Business-Aligned GRC
In the modern enterprise, risk does not respect organizational silos. A ransomware attack is not jus ...

-
 Shankar Jayaraman
Shankar Jayaraman - 22 Jul, 2025
Why Your GRC Tool Shouldn't Hold Your Keys? How CISOGenie is changing the game?
When I was a CISO, I found myself in a tough spot. I was really eager to find a GRC tool that could ...

-
 Shankar Jayaraman
Shankar Jayaraman - 14 Jul, 2025
Demystifying SEBI’s CSCRF
If you’ve ever stared at a SEBI circular wondering whether it’s written for lawyers, CISOs, or sup ...

-
 Shankar Jayaraman
Shankar Jayaraman - 14 Jul, 2025
16 Billion credentials leaked — Could poor Risk Management strategies be at fault
In mid-June, cybersecurity-focused news outlet Cybernews published a news article[[1]](https://cyber ...