Unified Risk Register (URR): From Siloed Risk Management to Business-Aligned GRC
-
 Balachandran Sivakumar
Balachandran Sivakumar - 19 Dec, 2025
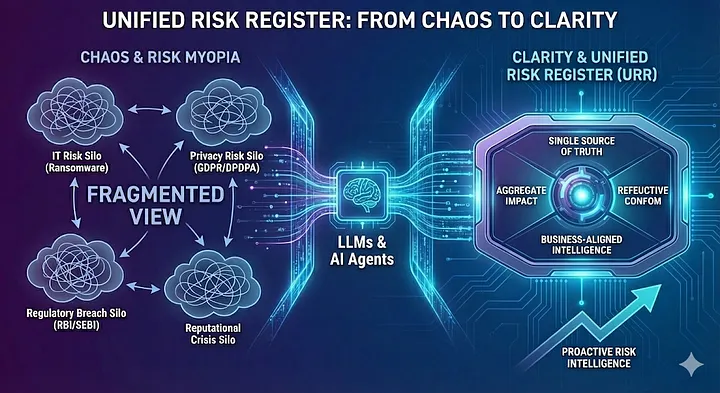
In the modern enterprise, risk does not respect organizational silos. A ransomware attack is not just an IT incident — it is a data privacy violation (DPDPA, for instance), a regulatory breach (RBI/SEBI), a financial blow, and a reputational crisis. Yet, most organizations continue to manage these exposures in fragmented lists: an IT Risk Register, a Vendor Risk Register (TPRM), a Privacy Impact Assessment list.
This fragmentation leads to “Risk Myopia”: the inability to see the aggregate impact of threats. This blog post makes the case for the transition to a Unified Risk Register (URR). By leveraging LLMs and Agentic AI, organizations can move from reactive compliance ticking to unified risk management, a way to achieve proactive, business-aligned risk intelligence.
The Rise and Fall of the Siloed Approach
Traditional GRC methodologies suggest specialized registers for specialized domains. This stems from the reasoning that each one owning the register has deep specialized knowledge of the domain and that would help us assess the risks with great depth and arrive at treatments.
While this eases the workload for specific department heads (because they just have to review in the context of their expertise), it creates systemic failure points for the Chief Information Security Officer (CISO) and the Board:
Duplication of Effort: A vendor failing a SOC 2 audit due to data processing concerns often triggers an entry in the Vendor Risk Register. But it also goes into the Privacy Risk Register and possibly the InfoSec Risk register too. Three teams effectively chase the same issue, wasting time and effort.
Inconsistent Scoring: A “High” risk in the IT register (based on CVSS scores) might be a “Low” risk in the Legal register (based on litigation probability). When we translate these to business use cases, prioritization becomes hard.
“Phantom” Risks: A risk mitigated in the Vendor Register (by choosing a different vendor, possibly) might still show up as open in the Privacy Register, due to communication breakdown (or any other reason). This ends up skewing the organization’s actual risk posture.
Regulatory Blindness: Regulations like the RBI Master Direction on IT Governance or SEBI’s CSCRF implicitly demand a holistic view of the supply chain and internal controls. Silos make compliance with these integrated frameworks nearly impossible to demonstrate in real-time.
The Paradigm Shift: Introducing Unified Risk Register
A URR is not simply merging Excel tabs into one giant sheet. It is a relational governance model.
It creates a “Single Source of Truth” where a risk scenario is defined once and mapped to multiple impact categories.
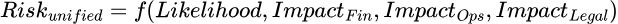
When we switch to URR, we take in, not the impact of just one team, but multiple teams. So, while a risk might be trivial to the Ops team, if it is critical to the Finance team, the URR will reflect that.
In the past, doing this was much harder because this involved significant manual effort. But the recent advancements in AI, particularly the advent of autonomous AI Agents has made this very easy to achieve.
Operationalizing the URR: How to Build It Effectively
Moving to a URR requires a shift in taxonomy and technology. Here is the blueprint for implementation:
1. Adopt a Common Language
You cannot unify registers if IT speaks “CVSS” and Legal speaks “Liability.” You must standardize the Risk Syntax.
- The “Cause”: What goes wrong? (e.g., Unpatched Server).
- The “Event”: What happens? (e.g., Data Exfiltration).
- The “Consequence”: What is the business hurt? (e.g., Financial fine under DPDPA).
2. Normalization of Scoring
We must normalize qualitative and quantitative scales.
- Example: If your TPRM tool uses a 1–100 scale, and your internal audit uses High/Med/Low, the URR must map them.
- Recommendation: Map everything to a 5x5 Matrix (Likelihood vs. Impact) quantified by financial tiers (e.g., Impact 5 = >$10M loss).
3. Anchor Risks to Business Processes, Not Assets & Systems
This is where traditional approaches fail, causing a lot of stress to CISOs. They link risk to a “Server” or a “Webapp”. A business leader does not care about the server; they care about the “Payment Processing Service.”
- The Hierarchy: Asset → Supports Process → Generates Revenue.
- The URR must show that if the Asset fails, the Revenue stops.
4. The “View” vs. The “Database”
A URR is the underlying database. However, the presentation should be filtered.
- The CISO View: Technical controls, CVEs, NIST 800–53 mappings.
- The Board View: Aggregate financial exposure, Top 5 Strategic Risks.
- The Privacy Officer View: PII data flow risks.
- It is the same data, sliced differently.
Strategic Advantages for the Business
- Explainable: When a regulator (RBI, SEBI, etc.) asks to show the Risk assessment, the URR provides a timestamped, consolidated audit trail of risk assessment, treatment plan and mitigation.
- Cost Optimization: By identifying that a given control (particularly when using cross-walks and CCF) satisfies requirements for ISO 27001, SOC 2, and HIPAA simultaneously, you avoid testing the same control three times. (Test Once, Comply Many).
- Speed: In multi-framework scenarios and highly regulated sectors, it is much faster to do risk assessments and come up with mitigation timelines when using a Unified Risk Register. In addition, this is a huge enabler for continuous risk assessment.
In Closing…
The CISO is now a business enabler. A Unified Risk Register is the tool that translates technical noise into business signals. It allows the organization to take calculated risks to grow, rather than avoiding risks out of fear and ignorance.
We believe that risk data should not die in a spreadsheet; it should live, breathe, and guide the enterprise toward resilience — this is the philosophy behind how we design CISOGenie